Cybersecurity is not the exclusive responsibility of specialists but an essential part of the business
In an increasingly digitalized world, cybersecurity has gone from being a technical concern to becoming a strategic priority.
With the sustained increase in cyber threats and the growing sophistication of attacks, Companies are investing more resources in protecting their data, infrastructure and operations.
What is interesting is that companies' interest in deploying cybersecurity strategies also focuses on their commercial objectives and levels of competitiveness.
Proof of this is that the 50% of Latin American companies report a total investment in cybersecurity of between 10 and 49 million dollars.
In Argentina, the 63% of companies implement cybersecurity tools.
While according to data shared by consultant Victor Ruiz in Infobae, 80.1% of people would stop purchasing products or services from a brand after a security incident.
To understand this context in greater depth, we share an exclusive conversation with Salvador Vial, Principal Executive Security Advisor and Field CISO of Amazon Web Services (AWS).
Together with him, we analyzed in detail the Challenges that organizations face in terms of cybersecurity, what are the most common cyberattacks and recommendations to improve resilience to this type of attack.
We also focused on the role that artificial intelligence plays in cybersecurity strategies, and the problem linked to the lack of professionals that the sector is experiencing.
We also discuss the concept of security by design, and share some insights into the interesting career of our interviewee.
A professional journey of multiple experiences with technology
Salvador's career began and continued over the years as a path of discovery. A multifaceted journey, which would lead to his consolidation as one of the Latin America's leading cybersecurity specialists.
In his early youth he chose to study electricity and electronics. At that time - 23 years ago - university courses linked to the field of technology were exclusively computer engineering courses oriented towards programming.
An area of expertise that was not of interest to him. He did not see himself programming all day.
This acquisition of theoretical knowledge and practical skills related to the design of electronic circuits - such as soldering boards - and working with motors and capacitor banks, together with power factor correction, was very useful to him years later, in the data center management.
Salvador's exploration also included CAD design programs for making electrical drawings, automation and control projects, and PLC systems.
All this background gave him a different perspective on how to manage emerging technologies.
The next step was to study network and telecommunications administration. But after completing that degree, he began working in a software quality assurance position. A position that was not related to networks.
“Having a broader knowledge can be a differentiator, but you have to be lucky enough to be able to exploit it,” he says.
In fact, he did not have the opportunity to apply his electrical knowledge until 15 years after having acquired it, when he began working for an electrical distribution company.
“Obviously everything is useful, it gives you another perspective. But you won't necessarily have to do a degree or study something and apply it directly,” he points out.
Today, Salvador, who defines himself as a restless person who likes to do different things, is happy with his career and his present. Especially with the possibility of getting involved in various projects, which are being developed in different countries.
In the future, he is interested in delving deeper into international business based on the versatility that comes from interacting with actors from all over Latin America.
Now that we have met our protagonist, let's move on to the analysis of his area of expertise in which he stands out today at Amazon Web Services (AWS).

What is a cyber attack?
A cyber attack can be carried out in many ways, using a variety of tactics or techniques. These include blocking access routes to a system to prevent users from operating it.
The purpose of denying access may be to obtain secret, classified or commercial information, or even to extort an organisation so that it can regain access to its data by paying a ransom.
The range of cyber attacks is wide and As technology evolves rapidly, so do digital criminal gangs..
“Much faster than private companies, and obviously faster than governments,” says Salvador. In this regard, he points out that cybercriminals do not carry out bidding processes to buy tools.
“They don’t spend six months buying a tool to help them defend themselves. They just pay a few dollars or cryptocurrency, get tools, and attack you.
It is much faster, much more agile the process they use. Whereas, On the side of those who defend, there are many administrative barriers that complicate", he warns.
At the end of the day, what matters comes down to three factors:
- The adaptability that organizations have through their processes.
- The current legislation, which can facilitate or obstruct cybersecurity work.
- The organizational culture developed in relation to cyber attacks, which consists of general knowledge and leadership exercised to improve cybersecurity standards.
This set of factors shows the speed and pace of how a company is defending its technology assets and digital business processes.
What are the most common cyber attacks?
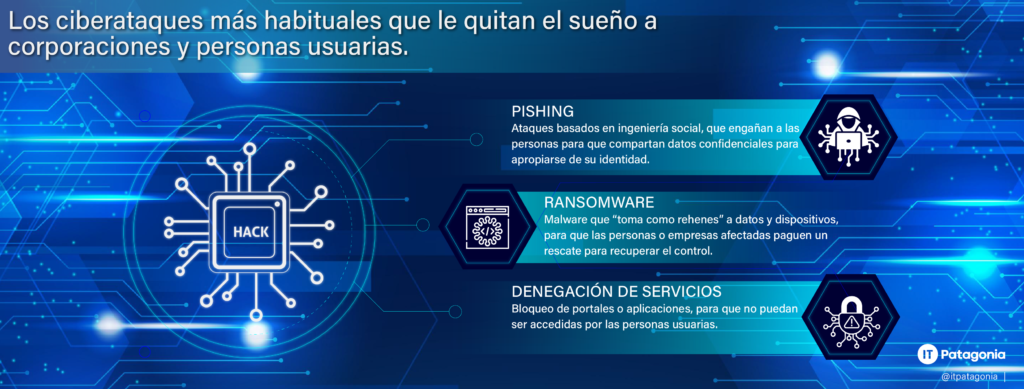
There are three major cyber threats or cyber attacks, which are the most common and frequent:
1) Phishing: It affects both corporations and users. It eventually leads to theft of information and subsequently to extortion.
2) Ransomware: carries out a destructive process targeting an organization's data. It can lead to extortion and ransom demands.
3) Denial of services: Block portals or applications so that they cannot be accessed.
What is the purpose of cyber attacks?
In the case of cyberattacks that result in extortion, the objective is the promise to stop the attack if the criminals meet a demand, which may consist of the payment of a ransom.
Another motivation may be to undermine a company's ability to generate loss of trust and undermine its image.
For example, if a bank is suffering a cyber attack, those who use its platforms and applications will be unable to make money transfers and transactions. It could even impact the institution's credit cards or other systems.
It can also happen with a government or other type of company.
The key is to understand that the question is not whether an organization will suffer a cyber attack, but when and how you will experience it. And even more importantly, how prepared it is to withstand it and respond to its consequences.
What is the volume of cyberattacks?
In recent years, Latin America has been gaining relevance in the cyber threat landscape.
In 2023 it was positioned as the fourth most attacked region worldwide, with Brazil leading at the regional level with 68% of cyberattacks, followed by Colombia (17%) and Chile (8%).
The information comes from the report IBM X-Force Threat Intelligence Index 2024, where it is reported that the cyber attacks with the greatest impact were the Data theft and data leakage, with 32% of incidents.
In fact, according to the report EY Global Cybersecurity Leadership Insights Study, 62% of Latin American companies suffered some type of data breach over the past year.
Definitely, The level of cyber attacks that occur daily around the world is very highBut the intensity varies according to the sectors.
In the case of financial institutions, which are the most commonly attacked organizations because they are big brands and process a lot of money, They can suffer 300 thousand attacks a month. All day, 24 hours a day..
“Criminals create automated robots that attack without resting, without blinking, and without eating,” says Salvador.
To combat these threats, it is necessaryThey need technical tools, trained professionals and the money needed to acquire cybersecurity solutions..
If we were to view the security strategy as a pyramid, all of these items would be at the base.
However, although it may be unnatural, what should be built first is not the base of the pyramid, but its head, based on two fundamental factors:
- How the company culture permeates cybersecurity concepts and puts them into practice.
- What is the leadership which is exercised from the top management of an organization, to put into practice the activities that need to be carried out.
In short, the key is the people And while corporate leadership is moving forward in raising awareness of the critical role it must play in the face of cyber threats, the pace is still not optimal.

At this point it is also worth mentioning the importance of considering in cybersecurity strategies the Legal aspects related to cybersecurity and data protection.
Just like the data governance, as the set of processes, policies, standards and metrics, which focus on ensure the quality, availability, integrity and security of data in an organization.
Even more so considering, as expressed in the whitepaper, Cybersecurity Futures 2030: New Foundations, that cyber security will go from being about the protection of confidentiality and availability of the information to be protected, its integrity and origin.
Who is leading the way in terms of cybersecurity?
Large corporations and business conglomerates are the organizations that today have the most developed defense capabilities against cyber attacks.
In particular, The financial industry, retail and mining companies stand out..
There are other types of industries that have been left behind, such as airlines and hotels.
While relevant sectors such as health and education also need to significantly improve their protection.
As for people, there are two very important drivers that are not being well developed today:
- Resources and recommendations on the proper use of technology should be offered in the educational field.
- Governments could launch campaigns to raise awareness about how to operate safely in the digital world. For example, in relation to digital procedures.
Security by design: How to make cybersecurity-friendly user experiences compatible?
In some organizations, there are leaders who believe that user experience and security are opposites. But it is quite the opposite. With Juan, we discovered that they do not need to be on opposite sides.
“The practice that should be used today in any institution that creates technology is the practice that in cybersecurity is known as security by design,” he says.
Because, if an organizational culture includes security by design in all its processes, Cybersecurity factors will be included in the user experience roadmap.
However, there is a discussion among leaders about how to implement security by design, because in practice, different teams perform both functions.
So there are many issues of coordination, leadership and communication to be resolved. But the methodology exists and the key to how to put it into practice.

Recommendations to improve resilience to attacks
Cybersecurity strategies must be led by the corporate management of organizations.
You can have a great team of cybersecurity specialists, but, If the drive does not come from the top and if there is no solid plan, the company will not be able to meet its objectives..
“Often, specialists and middle managers have very good technical ideas about cybersecurity, about how to implement controls in different systems and processes, but they do not have the strength to be able to execute them,” says Salvador.
Even if you have very good ideas, they will not be enough if you cannot obtain the appropriate budgets and ensure that all the teams in the organization are involved in the project.
In this context, It is important to have cybersecurity specialists who have the ability to implement the plan promoted by the management.
Always remembering that cybersecurity is not just a matter for the technical team. It obviously has to do with the technology area of an organization, but also with its business units.
Without this layer of articulation, technical teams would be disconnected from the reality of the company.
What role does AI play in cybersecurity strategies?
The artificial intelligence can help speed up the process automationFor example, situations that previously had to be controlled by a person can now be validated automatically by robots.
An AI robot can be asked to review documentation or a specific process, among other tasks. It can even provide a report in real time, a task that would take a person several hours of work.
AI can help automate those types of tasks and collaborate to alleviate the lack of professionals that exists in the field of cybersecurity.
These automations will give teams more time to focus on tasks where they can add greater value, instead of reviewing routine processes.
Is there a shortage of cybersecurity professionals?
There is a shortage of tens of thousands of cybersecurity specialists worldwide. This is a very large scale of unmet labour demand, and there is no way to fill the gap quickly.
"If we stick to the traditional way, for example, of training people in universities, it will probably take us 15 years to close the gap, and when we reach those 15 years we will have another gap, perhaps larger," warns Salvador.
One of the ways to alleviate this shortage of professionals is to focus on the methodological aspect.
In processes, in security by design and in organizational culture.
In contributing to ensuring that security issues are not perceived as matters exclusive to specialists but rather as an essential part of the business.
With the aim of reducing the technological talent gap, from IT Patagonia, together with our academic partner Codeki, one of the most relevant educational technology companies in the market, We promote the development of multigenerational talent to meet the needs of the industry.
Conclusion
The security approach must be shared by the entire organization.
Teams must have the same direction, the same goals, and even be measured by the same yardstick.Something that does not happen in many organizations, where cybersecurity KPIs are aimed only at the team of specialists, when they should involve business managers, so that they are the ones who drive the security methodology.
In this sense, we agree with Salvador in the Importance of continuous training and education to be prepared for cyber attacks, which, far from stopping, will continue to increase.

